Single Sign On (which is often confused with Social Sign-On) is a powerful functionality that can quickly increase company productivity and data security, centralise user password management, and make the life of IT teams much easier. In this post, I’ll explain the key difference between social sign-on and single sign-on, the benefits of setting up Salesforce with SSO, how it works, and how to set up Salesforce SSO with Office 365.
Single Sign-On vs. Social Sign-On: Key Difference
To clear the fog around these two terms, we need to understand their purpose and difference.
Single Sign-On (SSO) is an authentication process where users can log in to multiple applications from different devices using a single set of credentials like username, password, or token that you can generate, for example, in Microsoft Authenticator to log into the system.
Regarding Salesforce, you can make your Salesforce org a third-party identity provider to authenticate users. Or you can adjust a third-party app to log into Salesforce org.
A Social Sign-On (aka Social Login) – uses information from social networking sites such as Facebook, Twitter, and LinkedIn, to simplify logins on third-party applications and platforms.
You can spot such Facebook, Google, Twitter, and LinkedIn log in pages on sign-in/sign-up pages of eCommerce, news, and media websites.
Salesforce Social Sign-On is mainly used by Community users to log into Experience Cloud.
Why You Need SSO
The primary benefit of SSO is that it gives organisations centralized control of who has access and removes the need for users to log in to each system separately. It also helps
- Strengthen password policies
- Reduce the risk of a data breach and increase your organization’s security because you have external storage that can hardly be broken.
- Centralize access control
- Reduce IT workloads because your admins need to handle only one source of your passwords and credentials.
How Single Sign-On Works
To enable the SSO process, you need an Identity Provider- a trusted service that allows users to access other external applications without logging in again, and a Service Provider – a service that accepts identity on behalf of the external application from an identity provider.
In other words, the Identity Provider is a source of information about the user. So, when you log in via SSO, you log in to the Identity Provider, and the identity provider says to you if it’s a correct user or not.
How the whole process looks like:
- Step #01 – User accesses the Service Provider
- Step #02 – The Service Provider redirects the user to the Identity Provider
- Step #03 -User enters credentials
- Step #04 – The Identity Provider validates and grants access
- Step #05 – The Identity Provider redirects the user to the Service Provider
For example, you can configure Google G-Suite as an Identity Provider to authenticate users trying to access your org. When you log in to Salesforce, it automatically redirects you to your Identity Provider (in our case, this is G-Suite). There you’ll see login credentials such as a username and password, that you need to put in.
If you have the multi-factor authentication, you’ll receive an OTP that you need to put to log into G-Suite.
Once the process goes successfully, G-Suite will say that you are authenticated. It will also communicate to your Service Provider that you are allowed to use your Salesforce application as the Service Provider.
Requirements for SSO Enablement
There are specific provisions to enable SSO for Salesforce. Among them are:
- Admin Access: You must provide users with relevant access levels and the ability to configure certain functionality, which not necessarily have to be solely admin privileges.
- My Domain: You need to set up My Domain
- Sandbox: Your organization should have a Sandbox version to test everything there and to prevent breaking your login functionality for all users.
How to Configure Salesforce as the Identity and Service Provider
The most unique thing about Salesforce is it is an agile platform that you can configure as an identity provider, a service provider, or both.
Salesforce as the Identity Provider
You can set up a single identity provider to authenticate users for one or multiple service providers. For example, you can enable your Salesforce org as an Identity Provider and configure Microsoft Office 365 as the Service Provider, so users will be able access your org and Microsoft Office 365 with a single login. List of possible connections you can find here: https://help.salesforce.com/s/articleView?id=sf.identity_provider_examples.htm&type=5
Moreover, you can set up a single Logout to make users log out of a service provider and identity provider simultaneously.
You can configure Salesforce as an identity provider via several protocols: Security Assertion Markup Language (SAML), OAuth, and OpenID Connect. They are commonly used to connect Salesforce to some other tool and to configure a Single Sign-On.
Salesforce has a framework called – a Connected App – that enables an external application to integrate with Salesforce using APIs . With this Connected App, you can grant access to other Service Providers applications to use your Salesforce organization as the Identity Provider and log in with their Salesforce credentials.
You also can set up what the org users, what the application, and users of that application can do with your Salesforce data, for example, your standard objects.
Moreover, you can specify security policies like IP ranges from which the Service Provider can log in. Or you can restrict who can use this Connected App to, for example, only admin-approved users.
Salesforce as the Service Provider
You can configure Salesforce as a Service Provider for the most popular toolset – Google G-Suite. One of the benefits of using Google GSuite is that you can access your Salesforce organization via Chrome or other applications. More details on how to set up Salesforce with Google Single Sign On you may find in this post: https://www.salesforceben.com/set-up-salesforce-with-google-single-sign-on-sso/
Azure Active Directory is another identity solution that Microsoft provides. With the Active Directory, you can use all your Microsoft functionality like Office 365 or Microsoft Outlook. You can extend SSO with the help of Identity Connect and connect your Microsoft solution to your Salesforce to automatically log into your Salesforce organization via it.
https://help.salesforce.com/s/articleView?id=sf.sso_provider_azure.htm&type=5&language=en_US. And now we’ll tell you how to enable it step-by-step.
How to Set Up Salesforce with Microsoft Azure Active Directory Single Sign-On
The Azure application allows users to use their Azure Active Directory credentials to log in to a Salesforce org. There is an article provided by Salsforce how to do so, but it based on old Azure design. So, to activate this feature you need to:
- Log in to Microsoft Azure.
- On the menu, select Azure AD B2C, and select App registration.
- To register a new application, select New registration.
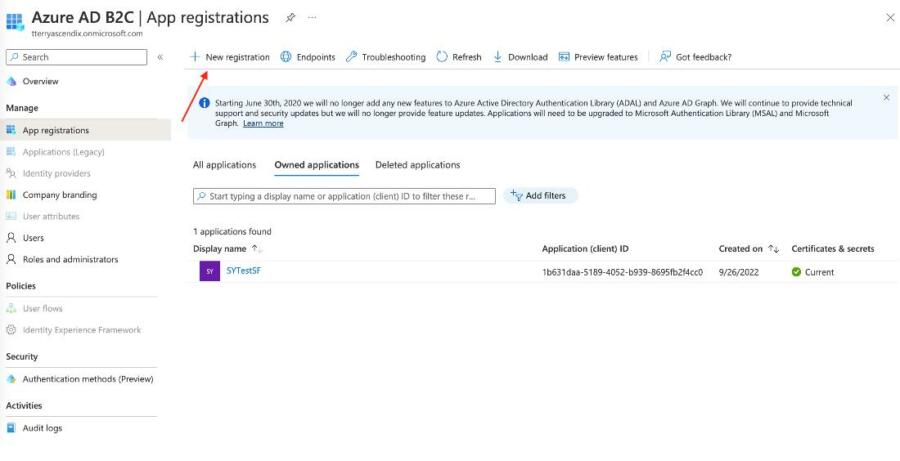
- Enter an application name, select Web app as the redirect URI, and enter https://salesforce.com as the sign-on URL. Click Register.
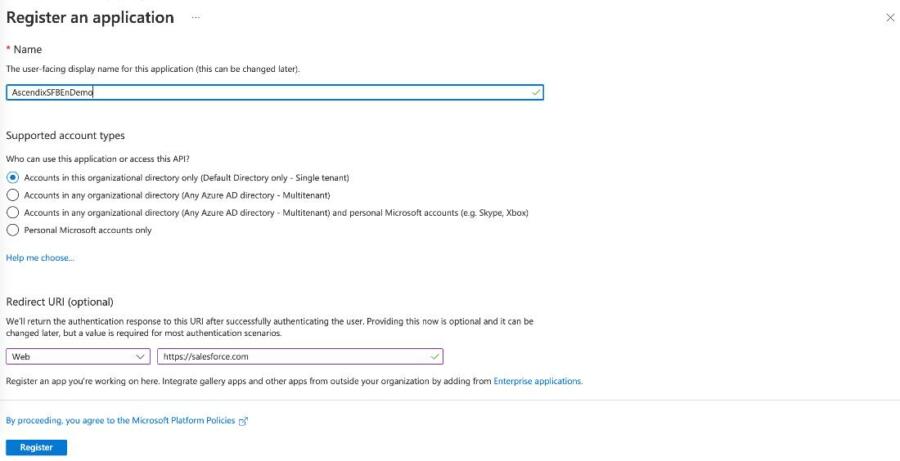
- Choose the application from the App registrations pane. Copy and save the Application ID, and then select Certificates & secrets.

- Enter a description and expiration date for the key. Save the settings, and copy the key value. To configure the authentication provider in Salesforce, use the key and application ID in the next step.

- Create default scope in expose an API
Now you need to go to Salesforce org.
- From Setup, enter Auth. Providers in the Quick Find box, and select Auth. Providers | New.
- For the provider type, select Open ID Connect.
- Enter a name for your Auth. Provider. Salesforce uses this name as the URL suffix in the callback URL, which is how the application responds to the Salesforce authentication request.
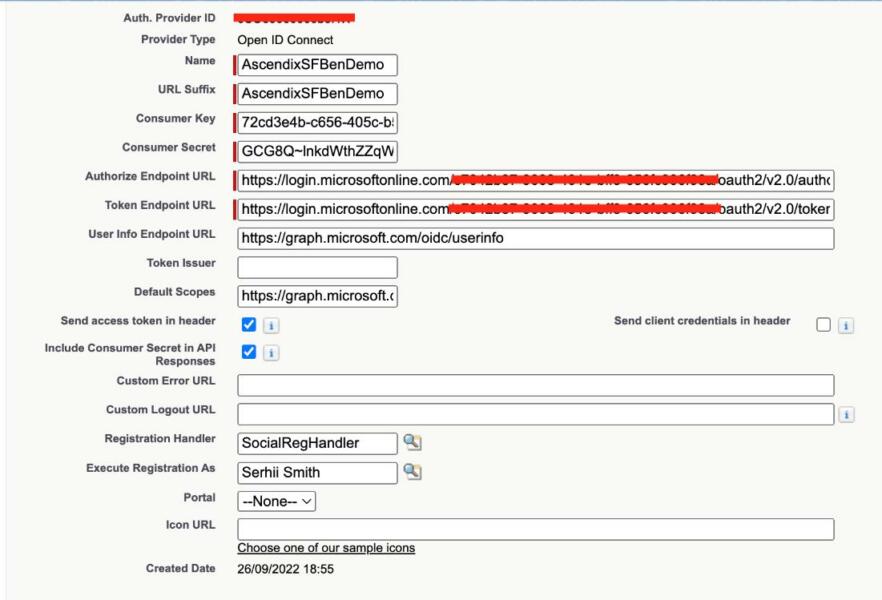
- For Consumer Key, paste the application ID that you copied earlier.
- For Consumer Secret, paste the key.
- For Default Scopes, paste API scope
- Enter the Azure AD endpoints. You can find them in Endpoints link:


- For User Info Endpoint URL you can use: https://graph.microsoft.com/oidc/userinfo
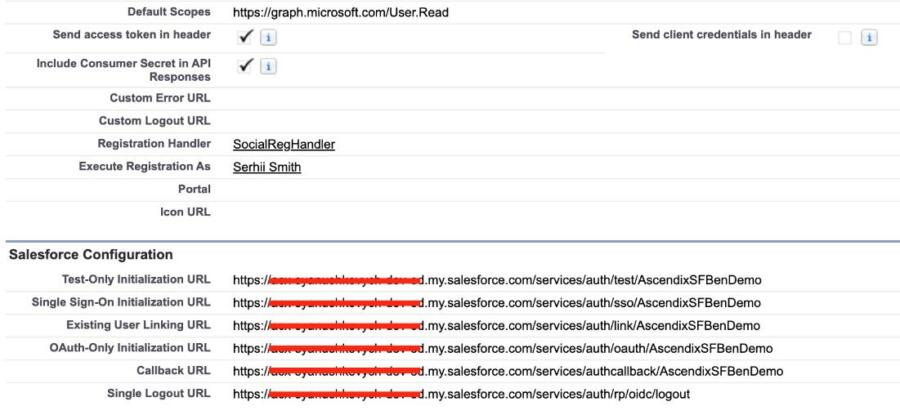
- For Default scope: https://graph.microsoft.com/User.Read
- Save the settings.
Now it’s time to update Your Azure Application with the Salesforce Callback URL
- On the Salesforce Auth. Provider page for Azure AD, copy the callback URL.
- In Azure AD, navigate to the Authentication tab and add new URL. Enter the Salesforce callback URL as a new reply URL and save the setting.

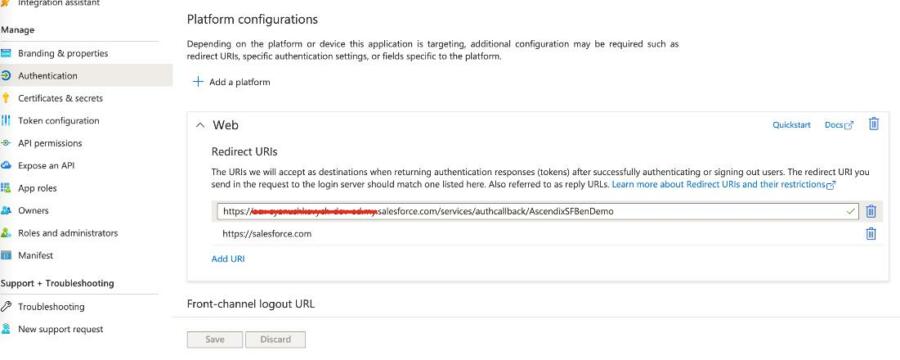
Create a Registration Handler
A registration handler is an Apex class that handles the heavy lifting of creating Salesforce users, updating users, and linking to existing users, accounts, and contacts. Example registration handlers are available as Apex classes on a GitHub site, including a SamlRegHandler and a SocialRegHandler. These handlers enable Salesforce SSO using Salesforce as an authentication provider or an external authentication provider.
- Download the social sign-on registration handler from GitHub:
- From Setup, in the Quick Find box, enter Apex Classes, and select Apex Classes | New. To create a registration handler for Azure, copy a sample Apex class (SocialRegHandler).
- On the Salesforce Auth. Provider page, edit the settings for the Azure AD Auth. Provider, and select the registration handler that you created.
- Enter a user for whom the registration handler executes, and save the settings
Let’s Test SSO with Azure AD
- In Setup, on the My Domain page under Authentication Configuration, click Edit.
- Select your Azure AD authentication service, and save the settings.

- Log out and go to your Salesforce org’s login page on your subdomain.
- Click the button for the Azure AD authentication service, and enter your Azure AD credentials.
The Final Words
Single Sign-On is a highly comfortable and helpful functionality that helps organisations with a lot of user management. Besides G-Suite and Azure Active Directory there are numerous other solutions on the market such as Okta and Amazon Web Services that you can use to enable Single Sign-On functionality.
So, if you need assistance with SSO activation or solution selection, you can seek external help with a Salesforce consulting agency like Ascendix. We have 26 years of CRM consulting experience under our belt and are certified Salesforce and Microsoft partners.
It allows us to ensure project success and eliminate all the issues that you may face dealing with any type of the system configuration.
Author Bio:
Sergiy Yanushkevich is a senior Salesforce app developer and software engineer at Ascendix Technologies, Salesforce evangelist, and an author of multiple guides on CRM optimization, integration, and security assessment.
Also read: Salesforce Testing: Types and Levels
























































