The Internet is becoming more dangerous, but services like HaveIBeenPwned (HIBP) attempt to assist. Personal data is being captured and exposed at an alarming rate, from the Yahoo hack to several recent ransomware assaults.
One security researcher, for example, gathered over 530 million names, email addresses, and phone numbers associated with firms such as Facebook, Twitter, and LinkedIn. It is difficult for businesses to protect their data entirely, but they could do a better job.
What Exactly is HaveIBeenPwned?
HaveIBeenPwned (www.haveibeenpwned.com) is a free website that searches several data breaches in one click to check if your information is among them. If this is the case, you can take precautions to reduce the possible harm. While the site’s developer, Troy Hunt, has stated that he does not believe in changing exposed passwords, you should be aware of it.
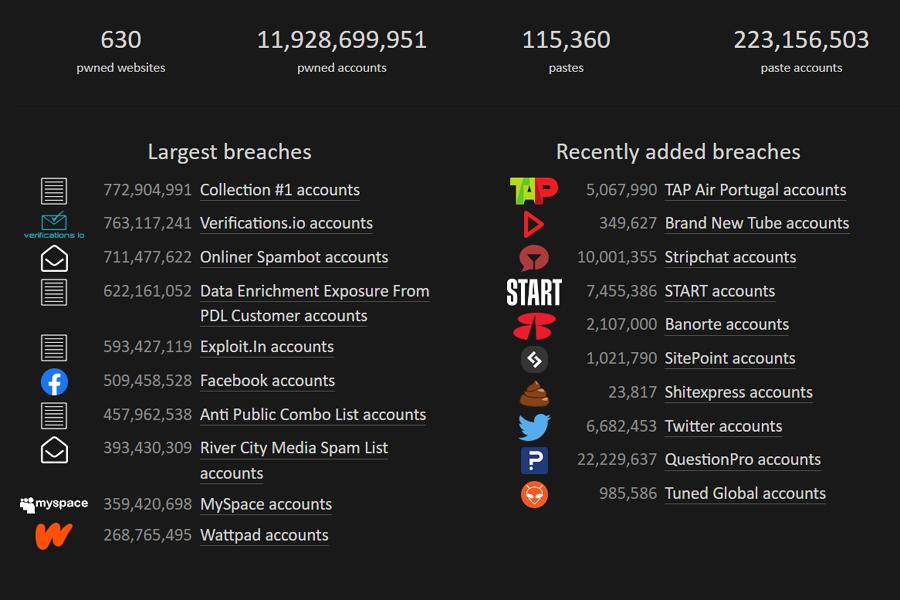
The site receives and adds data from large-scale data breaches regularly. When a new violation occurs, the HaveIBeenPwned database is updated. This database allows you to see if your email address is one of the approximately 6 billion accounts that have been compromised in some of the most severe breaches ever reported.
According to Hunt’s blog post announcing HaveIBeen Pwned in December 2013, the website was developed on his trip back from TechEd New Zealand 2013 and constructed overnight when he returned. Initially, it covered the Adobe breach, which had just been reported when Hunt was on the road, but he rapidly expanded it to include other breaches.
How to Use HaveIBeenPwned?
Have I Been Pwned is one of several tools available to help you secure yourself online, and it’s simple to use? Go to www.haveibeenpwned.com and put your email address into the search box. It will then check the Have I Been Pwned database for a match.
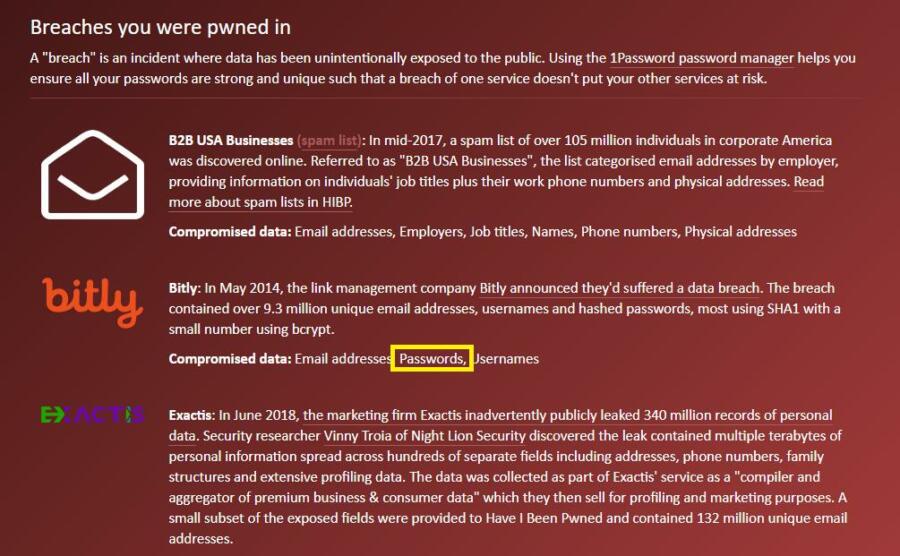
Aside from email addresses, Have I Been Pwned allows you to see if your password information has been compromised. On the navigation bar, select the “Passwords” tab. Next, input the password you believe has been leaked, and the system will verify their database.
You will also have access to a list of all essential data leaks that businesses have encountered. On the navigation menu, click the “Who’s been pwned” option to view a list of organizations, the breadth of the breach, and other details.
Have I Been Pwned offers a passive service in addition to active checks? You can set up notifications. If you subscribe to the site’s updates, you’ll receive an email whenever new information about a data breach that concerns you becomes available. These notifications, however, take time. It is normally many days after the first breach before any personal information is made public.
Is HaveIBeenPwned Legitimate and Secure?
It’s legal. Hunt collaborated with Google on the Password Alert Chrome extension, which compares your passwords to Have I Been Pwned’s database (Google uses this information anonymously). Using Have I Been Pwned should not jeopardize your security because the site does not retain your password and has security mechanisms to ensure that bots or other malicious users do not compromise it.
What Should You Do If You’ve Been Pwned?

It is not the world’s end if your personal information is compromised. While you can’t do much about your information once it’s out there, there are steps you can take after a data breach to protect yourself against identity theft and other concerns.
- Change your passwords: Although Hunt does not believe in changing passwords after the face, this is a good beginning step. Use a strong and unique password for each account to prevent one login from unlocking the others. If this sounds like a lot of work, think about using a password manager like NordPass or LastPass to keep track of everything.
- Increase the security of your account: Configure two-factor authentication (2FA) on all your accounts. This requires an extra code to validate your identity whenever you log in from a different device or location. Hackers will find it far more difficult to access your account using 2FA.
- Contact the impacted service: For more information, see the website of the firm that experienced the incident. The firm should provide information on determining if it exposed your individual data. It should also include a list of the following steps you must do. If the company’s website could be more helpful, try contacting them via social media.
- Look out for unusual activities: Keep an eye on your bank accounts and credit reports for any unusual changes or activities. If you see anything unusual, contact your bank right away. Credit monitoring services are accessible from respectable firms such as Equifax, Experian, and TransUnion.
What is Pwned and How Does It Relate to HIBP?
Pwned is a slang term derived from the word owned in leetspeak. The term “pwned” was initially used in an online game called Warcraft, where a map designer misread “owned.” From then, the term expanded and became a synonym for owned.
Unlike its core word, pwned does not suggest actual possession of something but rather the dominance or humiliation of an opponent. In online gaming, for example, pwning is humiliatingly one-sidedly beating someone (e.g., killing someone with a single shot).
Pwning can refer to breaching a computer system in hacker culture. If you hack into someone’s email account, you can remark, “I just pwned John’s email!” If you’re curious about leetspeak, there’s a handy leetspeak translator you can use.
HaveIBeenPwned: Final Verdict
Have I Been Pwned fills a critical public service void that governments and businesses have been hesitant to fill? If a corporation chooses to go public with a data breach, it may expose itself to litigation from aggrieved shareholders or consumers.
In most parts of the world, there are no rules requiring corporations to alert the public or their customers about a data breach. This is especially concerning for consumers who may be unaware that their personal information has been compromised and are thus at danger of being victims of identity theft or fraud.
Also read: Essential Features of a Good Email Marketing Service for an Online Store
























































